A new zero-day vulnerability has been disclosed for the Windows operative system. This is the fourth exploit disclosed in just as many months by the security researcher under the alias of SandboxEscaper. She first announced on December 25 that on New Year she would release publicly the PoC for a new bug in Windows, however jumped the gun and published the details just two days after.
On her tweet, she also mentions having informed the Microsoft Security Response Center (MSRC) about the bug “to give them a head start”. This is the second exploit published in December, after disclosing the code for another exploit that allowed reading protected files on December 19. Late August she published yet another exploit enabling privilege escalation allowing an attacker to elevate the access of malicious code from limited USER role to an all-access SYSTEM account, via a vulnerability in the Task Scheduler component, and in late October she presented yet another PoC for another privilege escalation bug, allowing to delete any file without permission.
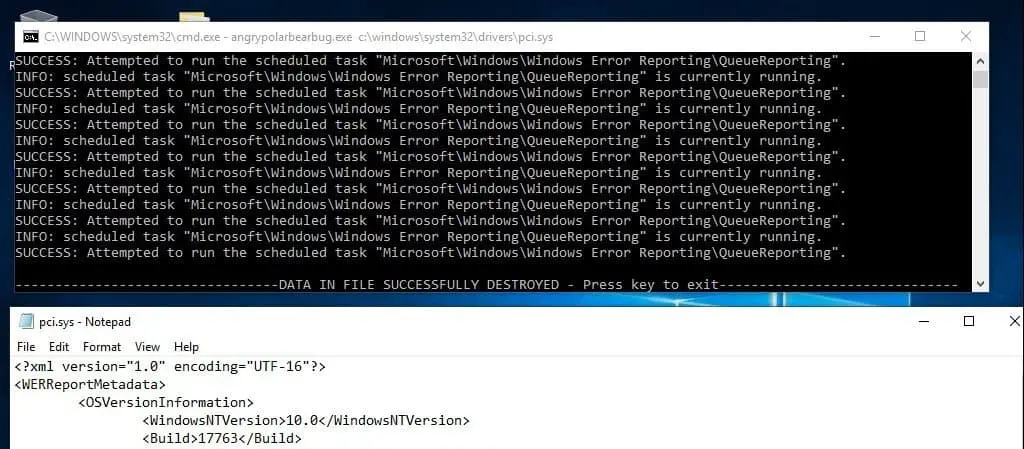
On the current exploit, running the proof-of-concept code provided results in overwriting ‘pci.sys’ with information about software and hardware problems, collected through the Windows Error Reporting (WER) event-based feedback infrastructure. The researcher warns that the exploit she wrote has some limitations and may not work with all CPU’s. She mentions how it she wasn’t able to reproduce the bug on a machine with only one CPU core.
SandboxEscaper also mentions how the bug isn’t always 100% effective, as it relies on a race condition, and wrong timings and the action of other operations may give a different outcome. However, the bug bounty programs don’t need a full exploit, they just need a PoC that allows understanding of the cause for a bug.
Will Dormann, a vulnerability analyst at CERT/CC who was able to reproduce the exploit on Windows 10 Home, build 17134 confirms this, mentioning on Twitter that the overwrite does not occur consistently.
This latest 0day from SandboxEscaper requires a lot of patience to reproduce. And beyond that, it only *sometimes* overwrites the target file with data influenced by the attacker. Usually it's unrelated WER data.https://t.co/FnqMRpLy77 pic.twitter.com/jAk5hbr46a
— Will Dormann (@wdormann) December 29, 2018
On a reply to the same Tweet, Mitja Kolsek, CEO of Acros Security, commented that 100% reliability does not matter if the attacker has a way to verify the success of the exploit.
This vulnerability may also be used to exploit other files, even deeming protection software useless, and performing other malicious actions on the Windows operative system.







